Understanding Zero Trust Security Models
In an era where cyber threats evolve rapidly, the Zero Trust Security Model emerges as a pivotal strategy for safeguarding digital assets. Unlike traditional security paradigms that operate on the assumption of trust within a network, Zero Trust mandates “never trust, always verify”. This article delves into the principles, implementation, and benefits of adopting a Zero Trust architecture, offering insights into its critical role in modern cybersecurity.
The Genesis of Zero Trust
The concept of Zero Trust Security Models emerged as a response to the limitations of traditional perimeter-based security, which relied on the outdated assumption that everything inside a network could be trusted. The idea was first formally articulated by John Kindervag, then a principal analyst at Forrester Research, in 2010. His groundbreaking work challenged the conventional “trust but verify” approach, arguing that implicit trust was a critical vulnerability in an era of sophisticated cyber threats.
The historical roots of Zero Trust can be traced back to earlier cybersecurity paradigms. In the 1990s, firewalls and VPNs dominated security strategies, creating a hardened perimeter while leaving internal systems exposed. High-profile breaches, such as the 2003 SQL Slammer worm and the 2008 Operation Aurora attacks, exposed the flaws in this model—attackers could move laterally once inside the network. These incidents underscored the need for a paradigm shift.
Key milestones in Zero Trust’s evolution include:
- 2010: Kindervag’s Zero Trust Architecture (ZTA) framework introduced the principle of “never trust, always verify.”
- 2014: Google’s BeyondCorp initiative demonstrated Zero Trust in practice, eliminating VPNs and enforcing access based on user and device context.
- 2020: The U.S. National Institute of Standards and Technology (NIST) published SP 800-207, formalizing Zero Trust guidelines for federal agencies.
The rise of cloud computing and remote work further accelerated Zero Trust adoption, as traditional network boundaries dissolved. Enterprises realized that security could no longer depend on physical perimeters but required dynamic, identity-centric controls. This shift marked a fundamental change in cybersecurity thinking—from guarding the castle walls to verifying every individual at every access attempt. The next chapter will explore how these ideas crystallized into the core principles that define Zero Trust today.
Core Principles of Zero Trust
Zero Trust security models are built on a set of core principles that fundamentally shift how organizations approach cybersecurity. Unlike traditional perimeter-based defenses, Zero Trust assumes no implicit trust—whether inside or outside the network. Instead, it enforces strict access controls and continuous validation to mitigate risks.
The first principle is least privilege access, which ensures users and devices only have the minimum permissions necessary to perform their tasks. This minimizes the attack surface by preventing unnecessary access to sensitive data or systems. For example, an employee in marketing should not have the same access rights as a system administrator. By implementing granular permissions, organizations can contain potential breaches and limit lateral movement by attackers.
Another critical principle is micro-segmentation, which divides networks into smaller, isolated zones. Each segment operates independently, requiring separate authentication before allowing communication between segments. This prevents threats from spreading across the network, even if one segment is compromised. Micro-segmentation is particularly effective in cloud environments, where dynamic workloads demand flexible yet secure boundaries.
Finally, continuous verification ensures that trust is never assumed but constantly reassessed. Every access request is evaluated in real-time based on user identity, device health, location, and behavioral analytics. If anomalies are detected—such as a login from an unusual location—access can be revoked immediately. This dynamic approach contrasts sharply with traditional models that grant persistent access after initial authentication.
Together, these principles redefine security by eliminating implicit trust and enforcing rigorous, context-aware controls. They form the backbone of Zero Trust, ensuring resilience against modern threats in an increasingly perimeterless digital landscape.
Zero Trust Architecture Explained
Zero Trust Architecture (ZTA) is built on a framework of interconnected components that work together to enforce strict security controls without relying on traditional perimeter defenses. At its core, ZTA hinges on identity verification, ensuring that every user, device, or application is authenticated and authorized before accessing resources. Multi-factor authentication (MFA) and identity-aware proxies play a critical role here, validating credentials in real-time while minimizing trust assumptions.
Another key pillar is device compliance checks, which assess the security posture of endpoints before granting access. This involves verifying patch levels, encryption status, and the presence of endpoint detection and response (EDR) tools. Non-compliant devices are either remediated or denied access, reducing the attack surface.
The architecture also leverages Secure Access Service Edge (SASE), a convergence of network and security services delivered via the cloud. SASE combines software-defined wide-area networking (SD-WAN) with Zero Trust principles, enabling secure access regardless of location. It enforces granular policies based on user identity, device health, and contextual factors like geolocation and time of access.
Integration of these components creates a dynamic security model where access is continuously reassessed. Micro-segmentation further isolates workloads, ensuring lateral movement is restricted even if a breach occurs. By weaving identity, device health, and SASE into a unified framework, Zero Trust Architecture eliminates implicit trust, replacing it with real-time, context-aware enforcement. This approach aligns with the principles discussed earlier while setting the stage for practical implementation strategies in the next chapter.
Implementing Zero Trust in Organizations
Implementing a Zero Trust model in an organization requires a structured approach that aligns technology, processes, and culture. The transition begins with planning and assessment. Conduct a thorough audit of existing infrastructure, identifying legacy systems, vulnerabilities, and access patterns. Map data flows and categorize assets based on sensitivity to prioritize protection efforts. This phase also involves defining policies for least-privilege access, ensuring users and devices only have permissions necessary for their roles.
Next, focus on technology selection. Deploy identity-centric controls like multi-factor authentication (MFA) and continuous authentication to verify users dynamically. Integrate device compliance checks to ensure endpoints meet security standards before granting access. Adopt micro-segmentation to isolate workloads and limit lateral movement. Solutions like Secure Access Service Edge (SASE) unify networking and security, enabling granular policy enforcement across cloud and on-premises environments.
A critical yet often overlooked aspect is the cultural shift. Zero Trust requires buy-in from leadership and employees. Educate teams on the principles of “never trust, always verify” to foster security awareness. Break down silos between IT, security, and operations teams to ensure cohesive implementation. Pilot Zero Trust in non-critical environments first, refining policies based on feedback before scaling organization-wide.
Finally, monitor and adapt. Continuous monitoring and analytics detect anomalies in real-time, enabling proactive responses. Regularly review access logs and adjust policies as threats evolve. Zero Trust is not a one-time project but an ongoing strategy that matures with the organization’s needs. By following these steps, businesses can systematically dismantle the traditional perimeter and build a resilient, adaptive security posture.
The Role of Identity and Access Management
In a Zero Trust security model, Identity and Access Management (IAM) serves as the foundation for enforcing the principle of least privilege. Unlike traditional perimeter-based security, where trust is implicitly granted once inside the network, Zero Trust requires continuous verification of identities and strict access controls. IAM ensures that only authenticated and authorized users, devices, and applications can access specific resources—nothing is trusted by default.
Key technologies underpin IAM in Zero Trust architectures. Multi-factor authentication (MFA) is essential, adding layers of verification beyond passwords, such as biometrics or one-time codes. This reduces the risk of compromised credentials granting unauthorized access. Similarly, single sign-on (SSO) streamlines secure access across multiple systems while maintaining centralized control over authentication policies. SSO minimizes password fatigue without sacrificing security, as each session is still subject to Zero Trust scrutiny.
Beyond authentication, IAM in Zero Trust includes dynamic access policies that adapt in real-time based on contextual factors like user location, device health, and behavior patterns. For example, an employee accessing sensitive data from an unrecognized device might trigger step-up authentication or outright denial. Role-based access control (RBAC) and attribute-based access control (ABAC) further refine permissions, ensuring users only access what they need for their tasks.
IAM also integrates with privileged access management (PAM) to secure high-risk accounts, enforcing just-in-time access and session monitoring. By tightly coupling IAM with Zero Trust principles, organizations can mitigate insider threats, credential theft, and lateral movement—critical as they transition to perimeterless security. The next chapter will explore how these IAM strategies extend to cloud environments, where identity becomes the primary security perimeter.
Zero Trust and Cloud Security
Zero Trust and Cloud Security: Securing Perimeterless Environments
The cloud’s dynamic, distributed nature makes traditional perimeter-based security obsolete. Zero Trust principles—never trust, always verify—are critical for protecting cloud-based assets, where workloads, data, and users span multiple environments. Unlike on-premises systems, cloud infrastructure lacks a fixed boundary, requiring granular controls that enforce least-privilege access and continuous authentication.
Key Challenges in Cloud Zero Trust Adoption:
- Ephemeral Workloads: Cloud instances spin up and down rapidly, making static security policies ineffective. Zero Trust mandates real-time visibility and dynamic policy enforcement.
- Shared Responsibility: While cloud providers secure infrastructure, customers must protect data and access. Zero Trust shifts focus to identity and workload-level controls.
- Multi-Cloud Complexity: Fragmented environments require unified policies. Solutions like Cloud Security Posture Management (CSPM) and Service Mesh architectures help enforce consistency.
Implementing Zero Trust in the Cloud:
- Microsegmentation: Isolate workloads using software-defined perimeters, reducing lateral movement risks.
- Identity-Centric Controls: Extend IAM (discussed earlier) with context-aware access, tying permissions to device health, location, and behavior.
- Encryption Everywhere: Protect data in transit and at rest, ensuring confidentiality even if perimeter defenses fail.
Cloud-native tools like Zero Trust Network Access (ZTNA) replace VPNs with granular, identity-based access, while Continuous Adaptive Risk and Trust Assessment (CARTA) frameworks dynamically adjust trust levels. As organizations embrace hybrid and remote work (covered next), these principles ensure security scales seamlessly beyond the cloud, adapting to an increasingly borderless digital landscape.
Zero Trust for Remote Workforces
The shift to remote and hybrid workforces has dismantled the traditional security perimeter, making Zero Trust an essential framework for safeguarding distributed environments. Unlike legacy models that assume trust based on network location, Zero Trust enforces strict verification for every access request, regardless of where it originates. This is critical for remote work, where employees connect from unsecured networks, personal devices, and diverse locations.
A key strategy for securing remote workforces is identity-centric security. Multi-factor authentication (MFA) and continuous authentication ensure that only verified users gain access. Role-based access control (RBAC) and least-privilege principles limit exposure, ensuring employees only access what they need. Additionally, behavioral analytics can detect anomalies, such as unusual login times or locations, triggering additional verification steps.
Endpoint security is another cornerstone. Remote devices must be continuously monitored and patched, with encryption enforced for data in transit and at rest. Zero Trust Network Access (ZTNA) solutions replace VPNs by providing granular, context-aware access to applications rather than broad network access. This minimizes attack surfaces and reduces lateral movement risks.
Finally, data-centric protection ensures sensitive information remains secure even if perimeter defenses fail. Data loss prevention (DLP) tools and encryption policies prevent unauthorized exfiltration, while micro-segmentation isolates critical assets.
As organizations embrace flexible work models, Zero Trust provides the adaptive security needed to protect assets beyond the corporate firewall. The next chapter will explore the challenges and misconceptions that can hinder Zero Trust adoption, offering solutions to navigate these complexities.
Challenges and Misconceptions
Adopting a Zero Trust security model is a transformative process, but it’s often met with resistance due to misconceptions and practical challenges. One common myth is that Zero Trust is solely about technology, when in reality, it requires a cultural shift within the organization. Employees and leadership must embrace the principle of “never trust, always verify”, which can disrupt traditional workflows. To address this, organizations should prioritize training and clear communication to align teams with the new security philosophy.
Another challenge is the perception that Zero Trust is too complex or expensive to implement. While the initial investment in identity and access management (IAM), micro-segmentation, and continuous monitoring tools can be significant, the long-term cost of a breach often outweighs these expenses. A phased approach—starting with critical assets and expanding gradually—can make adoption more manageable.
Many also mistakenly believe that Zero Trust eliminates the need for other security measures. In truth, it complements existing defenses like firewalls and endpoint protection by adding granular control. Organizations must avoid treating Zero Trust as a silver bullet and instead integrate it into a layered security strategy.
Finally, some assume that Zero Trust slows down operations due to frequent authentication requests. However, modern solutions like single sign-on (SSO) and adaptive authentication minimize friction while maintaining security. Balancing usability with protection is key—overly restrictive policies can lead to workarounds that undermine security.
By addressing these misconceptions and challenges head-on, organizations can pave the way for a smoother Zero Trust adoption, setting the stage for real-world success stories—as explored in the next chapter.
Case Studies and Real-World Applications
Many organizations have successfully adopted Zero Trust security models, demonstrating tangible benefits in real-world scenarios. Google’s BeyondCorp is a pioneering example, shifting from perimeter-based security to a device- and user-centric approach. By verifying every access request—regardless of origin—Google reduced reliance on VPNs and improved scalability. The key takeaway? Zero Trust enables secure remote work without compromising performance.
Another notable case is Microsoft’s implementation of Zero Trust, which integrated conditional access, multi-factor authentication (MFA), and continuous monitoring. Their approach minimized lateral movement threats by segmenting networks and enforcing least-privilege access. Microsoft reported a 50% reduction in security incidents post-implementation, proving that Zero Trust can significantly mitigate risks.
Financial institutions like JPMorgan Chase have also embraced Zero Trust to combat sophisticated cyber threats. By deploying micro-segmentation and behavioral analytics, they achieved granular control over sensitive data access. The lesson here is clear: Zero Trust is not just for tech giants—it’s scalable across industries with high-security demands.
In healthcare, Mayo Clinic adopted Zero Trust to protect patient data amid rising ransomware attacks. Their strategy included identity verification and real-time threat detection, ensuring compliance with HIPAA while maintaining operational efficiency.
Key lessons from these implementations:
- Start with identity and access management (IAM) as the foundation.
- Leverage automation for continuous monitoring and response.
- Prioritize user experience to avoid productivity trade-offs.
These case studies underscore that Zero Trust is not a theoretical ideal but a practical framework delivering measurable security improvements. As threats evolve, these real-world successes provide a blueprint for organizations aiming to transition from outdated perimeter defenses to dynamic, adaptive security models.
The Future of Zero Trust
The evolution of Zero Trust Security Models is poised to accelerate as emerging technologies and increasingly sophisticated cyber threats reshape the digital landscape. The future of Zero Trust will likely be defined by deeper integration with artificial intelligence (AI) and machine learning (ML), enabling real-time threat detection and adaptive access controls. AI-driven behavioral analytics will enhance identity verification by continuously monitoring user activities, flagging anomalies, and automatically adjusting permissions—reducing reliance on static policies.
Another critical development will be the convergence of Zero Trust with quantum-resistant cryptography. As quantum computing advances, traditional encryption methods may become obsolete, necessitating Zero Trust frameworks that incorporate post-quantum algorithms to safeguard data integrity. Additionally, the rise of edge computing and IoT ecosystems will demand Zero Trust architectures that extend beyond corporate networks, securing decentralized environments where perimeter-based defenses are ineffective.
The growing sophistication of cyber threats—such as AI-powered phishing and ransomware—will further drive Zero Trust adoption. Organizations will need dynamic, context-aware policies that respond to evolving attack vectors. For example, deception technologies could be embedded within Zero Trust frameworks to mislead attackers, while automated incident response systems will minimize breach impact.
Finally, regulatory pressures and industry standards will push Zero Trust from a best practice to a mandatory requirement. Governments worldwide are already advocating for Zero Trust in critical infrastructure, and frameworks like NIST’s SP 800-207 will continue to evolve, providing clearer implementation guidelines.
As Zero Trust matures, its principles will become foundational to cybersecurity, seamlessly blending with next-gen technologies to create resilient, adaptive defenses in an increasingly perimeterless world. The future lies not just in adopting Zero Trust but in making it an intrinsic part of organizational DNA.
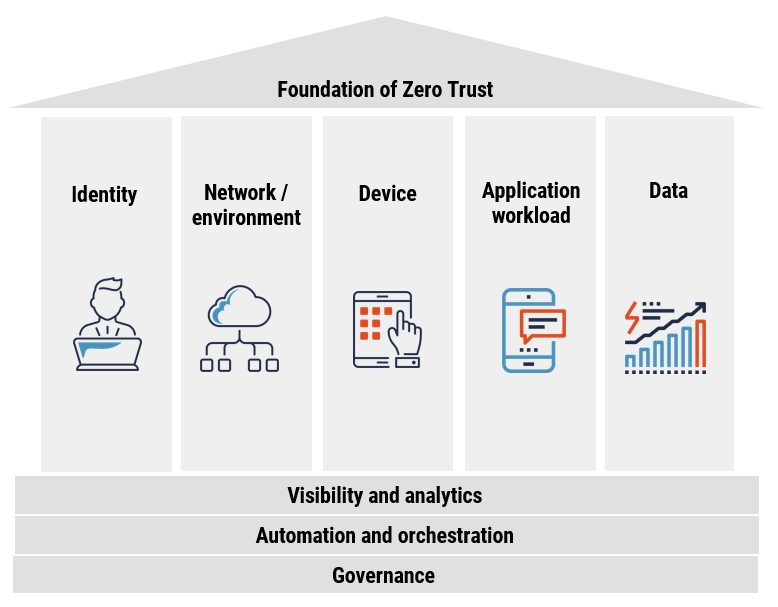
Conclusions
The Zero Trust Security Model represents a paradigm shift in cybersecurity, moving beyond outdated perimeter-based defenses to a more dynamic and resilient approach. By embracing the principle of “never trust, always verify”, organizations can significantly enhance their security posture in the face of sophisticated threats. As digital landscapes continue to evolve, Zero Trust stands as a critical framework for protecting assets in an increasingly interconnected world.



