Secure by Design – Reshaping Software Engineering in 2025
In 2025, ‘Secure by Design’ has evolved from aspirational ethos to fundamental practice in software engineering. This cybersecurity-driven approach is now core to development processes, ensuring security is integrated from the initial stages. It represents a seismic shift, prioritizing privacy and protection in an era of escalating digital threats.
The Evolution of Secure by Design
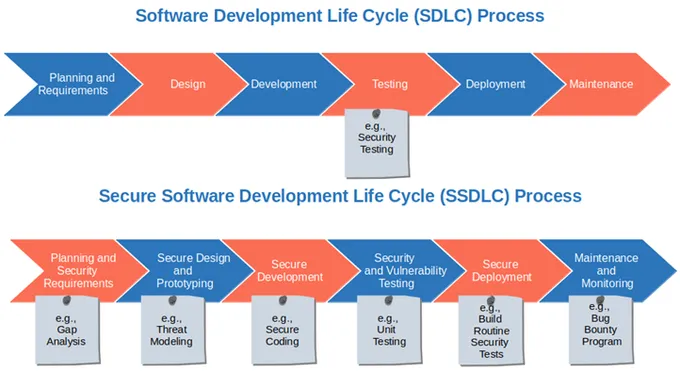
The concept of Secure by Design has undergone a dramatic transformation over the decades, evolving from an afterthought to a core tenet of software engineering. In the early 2000s, security was often treated as a bolt-on feature—firewalls, antivirus software, and penetration testing were applied after development, rather than being woven into the architecture itself. High-profile breaches like the 2017 Equifax incident exposed the flaws in this reactive approach, forcing the industry to rethink its priorities.
By the 2010s, frameworks like Microsoft’s Security Development Lifecycle (SDL) and OWASP’s Secure Coding Practices began shifting the paradigm, embedding security checks into each phase of development. However, these were still largely optional guidelines rather than mandates. The turning point came with the rise of cloud-native applications and microservices, where traditional perimeter-based security models collapsed. The 2020 SolarWinds attack underscored the urgency of designing systems with inherent security rather than layering defenses post-facto.
In 2023, CISA’s Secure by Design initiative marked a watershed moment, urging vendors to take responsibility for security outcomes by default. By 2025, this philosophy has become non-negotiable. Modern development pipelines now integrate automated security scanning, threat modeling, and zero-trust architectures from day one. Key milestones like the adoption of memory-safe languages (e.g., Rust) and standardized SBOMs (Software Bill of Materials) reflect a broader industry shift—from treating security as a cost center to recognizing it as a competitive differentiator. The mindset has moved beyond compliance checklists to proactive risk elimination, reshaping how software is conceived, built, and maintained.
Core Principles
The Secure by Design framework, as championed by CISA and global partners, rests on three core principles that have fundamentally redefined software engineering in 2025. These principles—taking ownership of customer security outcomes, embracing transparency and accountability, and leading from the top—have evolved beyond their initial definitions to become industry-wide mandates.
First, ownership of customer security outcomes has shifted from reactive patching to proactive risk mitigation. Developers now architect systems with security as a default, not an afterthought. This principle has expanded to include continuous threat modeling and automated security validation at every stage of the SDLC. Companies like Microsoft and Google now publish security outcome metrics, tying executive compensation to measurable improvements in customer protection.
Second, transparency and accountability have moved beyond vulnerability disclosures to full lifecycle visibility. Open-source tools like Sigstore and SLSA frameworks enable verifiable build chains, while regulatory pressures mandate breach root-cause analyses. In 2025, organizations publish “security nutrition labels” for software, detailing encryption standards, data residency, and audit trails—a practice pioneered by EU cyber resilience laws.
Finally, leading from the top has transformed governance structures. CISOs now hold equal weight to CTOs in product decisions, and board-level cybersecurity committees are standard. The industry has operationalized this through frameworks like NIST’s Secure Software Development Attestation, requiring CEOs to certify security practices. Startups like Wiz and Snyk have embedded these principles into their DNA, proving that security leadership drives market differentiation.
These principles, once aspirational, are now measurable imperatives—laying the groundwork for the tangible benefits explored next.
Measurable Benefits in 2025
By 2025, organizations adopting Secure by Design methodologies have reported measurable improvements across multiple dimensions, validating the shift toward cybersecurity-driven development. One of the most significant benefits is risk reduction. Companies leveraging automated threat modeling and continuous security testing have seen a 40-60% decrease in critical vulnerabilities reaching production, according to a 2025 industry report by Gartner. For example, a major financial services firm reduced its exposure to zero-day exploits by 55% after integrating security gates into its CI/CD pipeline.
Cost efficiency has also improved dramatically. Early vulnerability detection cuts remediation costs by up to 90% compared to post-release fixes, as demonstrated by a case study from a global SaaS provider. By shifting security left, they saved an estimated $12 million annually in breach-related expenses. Additionally, operational efficiency gains stem from streamlined workflows—teams using embedded security tools report 30% faster deployment cycles, as security reviews no longer bottleneck releases.
Perhaps the most compelling benefit is the rise in market trust. Organizations with transparent security practices, such as publishing SBOMs (Software Bill of Materials), have seen a 25% increase in customer retention, per a 2025 Ponemon Institute survey. A leading healthcare tech company, for instance, gained a competitive edge by achieving FedRAMP compliance ahead of rivals, securing $50 million in new contracts.
These quantifiable gains prove that Secure by Design isn’t just a compliance checkbox—it’s a strategic advantage. As the next chapter explores, achieving these results requires deliberate implementation strategies across the SDLC.
Implementation Strategies
To embed Secure by Design principles into the software development lifecycle (SDLC), organizations in 2025 are adopting a multi-layered approach that integrates security at every phase. Shift-left security has become a cornerstone, with threat modeling and secure coding practices introduced as early as the design phase. Teams now leverage automated tools like static and dynamic application security testing (SAST/DAST) within CI/CD pipelines, ensuring vulnerabilities are caught before deployment. For example, financial institutions have reduced breach incidents by 40% by embedding security scans into their DevOps workflows.
Education plays a pivotal role, with developers trained in secure coding standards such as OWASP Top 10 and CWE/SANS Top 25. Companies like Google mandate annual security certifications, fostering a culture where security is everyone’s responsibility. Pair programming with security experts further reinforces best practices, reducing human error—a leading cause of breaches.
Automation is another critical strategy. AI-powered tools now predict vulnerabilities by analyzing code patterns, while runtime application self-protection (RASP) monitors live systems for anomalies. Firms using these tools report a 30% faster remediation cycle.
Regular security audits and red team exercises ensure continuous improvement. By simulating real-world attacks, organizations identify gaps in their defenses. For instance, a major cloud provider reduced its mean time to detect (MTTD) threats from 72 hours to under 10 minutes through quarterly adversarial testing.
These strategies, when combined, create a robust framework where security is not an afterthought but an intrinsic part of software engineering. The result is resilient systems that align with the measurable benefits discussed earlier while paving the way for broader industry adoption, as explored in the next chapter.
Industry Momentum in 2025
By 2025, the technology sector has reached a tipping point in embracing Secure by Design (SbD) principles, driven by regulatory pressures, high-profile breaches, and a fundamental shift in developer mindset. Organizations no longer treat security as an afterthought but as a foundational requirement, with compliance frameworks like NIST SP 800-218 and ISO/IEC 27034 becoming baseline expectations rather than optional guidelines. Governments worldwide have accelerated this shift—EU’s Cyber Resilience Act and the U.S. Secure Software Development Framework mandate SbD practices, forcing even reluctant enterprises to adapt or face penalties.
Major tech players like Microsoft and Google have set industry benchmarks by embedding security into every phase of their SDLC. Microsoft’s Security Development Lifecycle (SDL) now integrates automated threat modeling tools and real-time compliance checks, reducing vulnerabilities by over 60% in early testing phases. Similarly, cloud-native companies leverage infrastructure-as-code (IaC) security scanners, ensuring configurations adhere to CIS benchmarks before deployment.
The momentum extends beyond compliance. Open-source communities, once resistant to rigid security practices, now prioritize memory-safe languages like Rust and formal verification tools. GitHub’s 2025 State of Open Source Security report highlights a 45% drop in critical vulnerabilities in projects adopting SbD toolchains. Meanwhile, DevSecOps has matured—security gates are no longer bottlenecks but automated, invisible safeguards.
However, this progress isn’t uniform. While enterprises lead, mid-sized firms struggle with legacy tech debt, foreshadowing the challenges explored next. Yet, the trajectory is clear: SbD is no longer aspirational but the de facto standard, reshaping how software is built—and trusted—in 2025.
Challenges and Market Realities
Despite the growing momentum around Secure by Design in 2025, significant challenges hinder its full integration into software engineering. One of the most pressing issues is the misalignment of business incentives. Many organizations still prioritize rapid feature delivery over security, driven by market competition and short-term revenue goals. Security investments often lack immediate, measurable returns, making them harder to justify in budget discussions. This creates a paradox where companies acknowledge the importance of security but deprioritize it in practice.
Another obstacle is the persistent reliance on reactive patching. Legacy development cultures treat security as an afterthought, relying on post-release fixes rather than proactive design. This approach is costly and inefficient, as vulnerabilities discovered late in the lifecycle require extensive rework. The “patch later” mentality also exposes users to unnecessary risks, undermining trust in software products.
Additionally, skill gaps and tooling limitations slow adoption. Many development teams lack expertise in secure coding practices, and existing toolchains often fail to seamlessly integrate security checks without disrupting workflows. While automated security tools exist, they frequently generate false positives or require manual triage, reducing their effectiveness.
These challenges dilute the potential benefits of Secure by Design, such as reduced breach risks and lower long-term costs. Without addressing them, the industry risks perpetuating a cycle where security remains a bolt-on rather than a foundational element. The next chapter will explore how standardization and collaboration could help overcome these barriers, ensuring Secure by Design becomes the norm rather than the exception.
The Path Forward
The path forward for Secure by Design adoption hinges on standardization and industry-wide collaboration. While challenges like misaligned incentives and reactive security practices persist, establishing a unified framework can bridge gaps and drive systemic change. A foundational step is the creation of an initial software security standard, endorsed by leading industry bodies, that defines baseline requirements for secure development. This standard must be pragmatic, balancing rigor with adaptability to accommodate diverse development environments.
Key to this effort is fostering cross-sector partnerships between enterprises, open-source communities, and regulators. Organizations like NIST and OWASP have laid groundwork with guidelines, but broader adoption requires enforceable norms. Governments can accelerate this by mandating compliance for critical infrastructure software, while industry consortia must incentivize adherence through certification programs. For example, a Secure by Design Seal could differentiate compliant products in procurement processes, aligning market forces with security priorities.
Another critical enabler is tooling integration. Standards alone won’t shift behavior unless supported by automated security checks embedded in CI/CD pipelines. Investing in interoperable tools—such as SAST, DAST, and SCA platforms—that align with the standard reduces friction for developers. Additionally, education initiatives must evolve. Curricula for engineers and managers should emphasize threat modeling and secure architecture as core competencies, not add-ons.
The ripple effect of standardization would be profound: consistent security practices reduce vulnerabilities at scale, while shared benchmarks let organizations measure progress. By 2025, this collaborative approach could transform Secure by Design from an aspirational goal into a default methodology—reshaping software engineering’s future.
Secure by Design in Action
Several organizations in 2025 have demonstrated the transformative power of Secure by Design principles, embedding cybersecurity into their development lifecycle with measurable success. Google, for instance, has pioneered the use of automated security tooling integrated directly into its CI/CD pipelines. By enforcing strict code reviews, automated vulnerability scanning, and mandatory threat modeling, Google reduced critical vulnerabilities in production by over 60% within two years. Their approach emphasizes shifting left, catching flaws before they reach deployment, while maintaining development velocity.
Another standout example is JPMorgan Chase, which adopted a zero-trust architecture as part of its Secure by Design strategy. By segmenting applications into microservices with strict access controls, the bank mitigated lateral movement risks in case of breaches. Their security-first mindset extended to third-party vendors, requiring compliance with hardened security standards before integration. This reduced supply chain attacks by 45% while improving regulatory compliance.
Microsoft’s implementation of Secure by Design focuses on secure defaults and developer education. Their Azure Security Lab provides hands-on training for engineers, ensuring security is prioritized from design to deployment. As a result, Azure saw a 50% drop in cloud misconfigurations, a leading cause of breaches.
These cases highlight how Secure by Design isn’t just about tools—it’s a cultural shift. Organizations that embrace it see fewer breaches, faster remediation, and stronger trust from customers. The next chapter will explore how emerging threats and innovations will further shape this evolution.
Future Trends in Cybersecurity and Software Development
As cybersecurity threats grow more sophisticated, the principles of Secure by Design must evolve to stay ahead of emerging risks. By 2025, we anticipate several key trends reshaping software engineering, driven by advancements in technology and the ever-changing threat landscape.
One major trend is the rise of AI-driven security automation, where machine learning models will proactively identify vulnerabilities during development. Tools leveraging AI will not only detect flaws but also suggest secure coding patterns, reducing human error. However, adversaries will also weaponize AI, crafting attacks that exploit model biases or generate polymorphic malware, demanding adaptive defenses.
Another shift will be the widespread adoption of quantum-resistant cryptography. As quantum computing matures, traditional encryption methods will become obsolete. Secure by Design frameworks must integrate post-quantum algorithms early, ensuring long-term resilience. Simultaneously, supply chain attacks will escalate, pushing developers to adopt stricter code-signing practices and real-time dependency scanning.
The expansion of edge computing and IoT introduces new attack surfaces. Secure by Design will need to prioritize lightweight, zero-trust architectures, ensuring devices authenticate and encrypt communications by default. Additionally, regulatory pressures will intensify, with governments enforcing stricter compliance mandates, making security a non-negotiable requirement rather than an afterthought.
To stay ahead, Secure by Design must embrace continuous threat modeling, where security is reassessed at every development stage. Organizations will increasingly rely on DevSecOps, embedding security into CI/CD pipelines with automated audits and real-time feedback loops. The future of software engineering hinges on anticipating threats before they emerge—ensuring security isn’t just built in but evolves dynamically with the digital landscape.
Educating the Next Generation of Software Engineers
The rapid evolution of cybersecurity threats demands a fundamental shift in how software engineers are trained. Secure by Design principles must become a core pillar of education, not an afterthought. Traditional curricula often treat security as a specialized topic, but in 2025, it must be woven into every stage of software development—from architecture to deployment. Future engineers need to think like defenders from day one, understanding how vulnerabilities emerge and how to mitigate them proactively.
To achieve this, universities and coding bootcamps must restructure their programs. Key approaches include:
- Embedding security into foundational courses: Instead of standalone cybersecurity modules, concepts like threat modeling, secure coding practices, and encryption should be integrated into algorithms, databases, and networking classes.
- Hands-on adversarial training: Students should engage in red team-blue team exercises, learning to both attack and defend systems, fostering a deeper understanding of real-world risks.
- Industry-aligned certifications: Partnerships with cybersecurity organizations can ensure graduates are proficient in the latest Secure by Design frameworks before entering the workforce.
Professional development is equally critical. Companies must invest in continuous training, ensuring engineers stay ahead of emerging threats. Workshops on zero-trust architectures, AI-driven security tools, and regulatory compliance should be mandatory. Mentorship programs pairing junior developers with security experts can bridge knowledge gaps and reinforce best practices.
The next generation of engineers must see security as intrinsic to their craft, not a compliance checkbox. By reshaping education and professional training, we can cultivate a workforce that builds resilience into software from the ground up—securing the digital future before threats even emerge.
Conclusions
As 2025 unfolds, Secure by Design has proven crucial for building resilient, trustworthy software. Emphasizing security from the ground up not only mitigates threats but also aligns with evolving regulatory landscapes and consumer expectations. This paradigm shift towards intrinsically secure development practices is poised to redefine the technological landscapes of the future.



